
Navigating the Bluetooth LE Data Transport Architecture
September 12, 2024

In the intricate world of wireless communication, the efficiency and reliability of data transport Architecture are paramount. Bluetooth Low Energy (BLE) has risen to prominence, offering a sophisticated yet energy-efficient solution for data transport in various applications. At the core of BLE’s success is its Data Transport Architecture, which facilitates the movement of data packets across devices. This article provides an in-depth exploration of BLE’s Data Transport Architecture, discussing its components, mechanisms, and the role it plays in ensuring efficient data communication.
The Underpinnings of Data Transport in BLE
The Data Transport Architecture in BLE is designed to accommodate the needs of low-power, low-data rate applications while maintaining high reliability. It operates on a connection-oriented basis, where devices establish a connection before data exchange commences. This architecture is composed of several key elements, including the Logical Link Control and Adaptation Protocol (L2CAP), the Attribute Protocol (ATT), and the Generic Access Profile (GAP).
Logical Link Control and Adaptation Protocol (L2CAP)
L2CAP is a critical component of BLE’s Data Transport Architecture, sitting atop the Link Layer and below the ATT. It provides the necessary protocols to segment, reassemble, and multiplex higher-level protocol data over BLE links. L2CAP ensures that data is efficiently transported across the potentially unreliable nature of wireless links by offering flow control and error handling mechanisms.
Flow Control
Flow control is essential in managing the pace at which data is sent across a BLE link, preventing the sender from overwhelming the receiver. L2CAP achieves this through a credit-based system, where the receiver advertises the amount of data (in bytes) it can accept, thus controlling the flow of data.
Error Handling
To maintain data integrity, L2CAP includes error detection and handling mechanisms. It uses sequence numbers to ensure that data packets are received in order and can request retransmission of lost or corrupted packets.
Attribute Protocol (ATT)
The ATT is a higher-level protocol that operates over L2CAP, responsible for the exchange of data between devices. It defines the structure and operations of the data being exchanged, known as attributes. These attributes are used to represent the characteristics of a device, such as its services and their corresponding characteristics.
Attribute Operations
ATT supports a range of operations, including read, write, and notification procedures. These operations allow devices to query and update each other’s attributes, facilitating the dynamic exchange of information.
Efficient Data Exchange
ATT is designed to minimize the amount of data transmitted, using techniques such as attribute handles and UUIDs to reference data, rather than transmitting the entire data set each time.
Generic Access Profile (GAP)
GAP defines the roles that devices can assume during communication, such as broadcaster, observer, peripheral, and central. It also manages the procedures for device discovery and connection establishment, which are prerequisites for data transport.
Discovery Procedures
Before data transport can occur, devices must discover each other. GAP facilitates this through procedures like advertising and scanning, where devices broadcast their presence and other devices scan for these broadcasts.
Connection Establishment
Once a device is discovered, a connection must be established for data transport to commence. GAP defines the procedures for this, including connection initiation, parameter negotiation, and connection update.
Data Transport Mechanisms
BLE’s Data Transport Architecture employs several mechanisms to ensure efficient and reliable data transport.
Asynchronous Connection-Oriented (ACL) Data Packets
The most common method of data transport in BLE is through ACL data packets. These packets are used for data that can tolerate some delay, such as sensor data or notifications.
Broadcast Data Packets
For connectionless data transport, such as advertising a device’s presence, broadcast data packets are used. These packets are transmitted on specific advertising channels and can be received by multiple devices.
Isochronous Data Packets
Isochronous data packets are used for data that requires timely delivery, such as audio streaming. These packets are transmitted on a regular schedule, ensuring that data arrives within predictable timeframes.
Challenges and Solutions
The Data Transport Architecture in BLE faces challenges such as limited bandwidth, the potential for data loss, and the need for low latency in certain applications. To address these challenges, BLE employs solutions like:
Adaptive Data Rate (ADR)
BLE can adjust its data rate based on the quality of the connection, allowing for higher data rates when the link is strong and lower rates when it is weak.
Enhanced Retransmission Mechanisms
To combat data loss, BLE uses enhanced retransmission mechanisms that can quickly recover from packet loss by requesting retransmissions of missed packets.
Low Latency Modes
For applications requiring low latency, BLE offers modes that prioritize timely data delivery, such as the use of isochronous data packets.
The Future of BLE Data Transport Architecture
As technology advances, the BLE Data Transport Architecture continues to evolve. Future developments may include support for higher data rates, improved error correction techniques, and more efficient data multiplexing methods.
Conclusion
The Data Transport Architecture in Bluetooth Low Energy is a testament to the protocol’s flexibility and efficiency. It provides a robust framework for devices to communicate, ensuring that data is transported reliably and efficiently, even in the face of the challenges inherent to wireless communication. As BLE continues to be a driving force in IoT and wearable technology, its Data Transport Architecture will remain a critical component of its success.
Leave a Reply
Related Products
You Might Like Also

In the intricate world of Bluetooth Low Energy (BLE) communications, the Generic Attribute Profile (GATT) plays a pivotal role in defining the structure and methods for data exchange. Central to this are the processes of Notifications and Indications, which are the primary means by which GATT servers update clients about changes in attribute values Read More
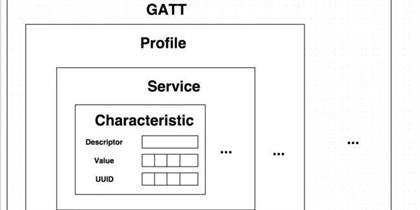
Central to BLE’s functionality is the BLE Generic Attribute Profile (BLE GATT), which serves as the protocol’s backbone, enabling efficient and structured data communication between devices. This article aims to provide an in-depth exploration of GATT, its components, and its role in BLE technology. Read More
In the realm of wireless communication, Bluetooth advertising has carved out a niche for itself, becoming an indispensable technology for short-range connectivity. At the heart of Bluetooth functionality lies the advertising process, which is the cornerstone for device discoverability and connection establishment. This article delves into the intri Read More
Bluetooth data structures are the foundational elements that govern how data is packaged, transmitted, and received within the Bluetooth ecosystem. These structures are designed to optimize the efficiency and reliability of wireless communication, ensuring that data is handled effectively across various devices and platforms. Read More
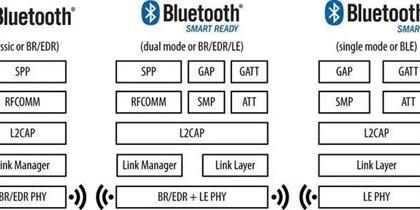
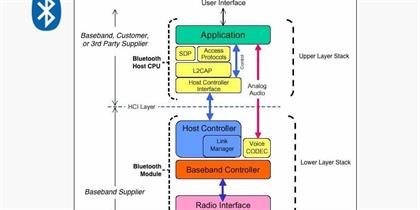
In the intricate world of wireless communication, Bluetooth Protocol Stack has established itself as a cornerstone technology, facilitating seamless connectivity between a plethora of devices. At the heart of this technology lies the Bluetooth protocol stack, a structured set of protocols that govern how devices communicate. One of the most critica Read More

In the intricate world of wireless communication, the Bluetooth Generic Access Profile (Bluetooth GAP) of Bluetooth technology stands as a cornerstone, enabling devices to connect, communicate, and collaborate seamlessly. This article delves into the essence of Bluetooth GAP, its role in establishing connections, and the myriad ways it enhances our Read More











